A Journey to the Firmware of ZTE H267A: Part III
Let’s summarize all the information we have so far.
- The router makes
httprequestshttp://acs.superonline.net:8015/cwmpWeb/WGCPEMgtto get configuration server URL - In the response returned, we found
https://acs.superonline.net/cwmpWeb/CPEMgt(port 443) as configuration server URL which force router to use TLS connection acs.superonline.netdomain has another open port to use to access configuration server which is8010- We have PPPoE Server named
ppp0, PPPoE Client namedppp1, and we forwarded all the packets throughppp1interface usingiptables
With all these pieces of information collected, I was ready to start getting the data I needed in the first place.
Altering the Response
As I mentioned in the previous part, I need a proxy tool to alter the response, and I chose to use Mitmproxy.
Installed, and started it with --replace parameter.
The meaning of this parameter is to filter only response bodies, if there is a matching string with the first part, replace it with the second part.
|
|
And now, the only thing needed was, forwarding all the requests going to port 80, 8010, and 8015 to mitmproxy, so it can alter the response for us.
|
|
Searching for the Root Password
Opened up Wireshark, started capturing the interfaces that cables connected before, and reset the router to factory settings.
After a couple of minutes, there were lots of http packets going to http://acs.superonline.net:8010.
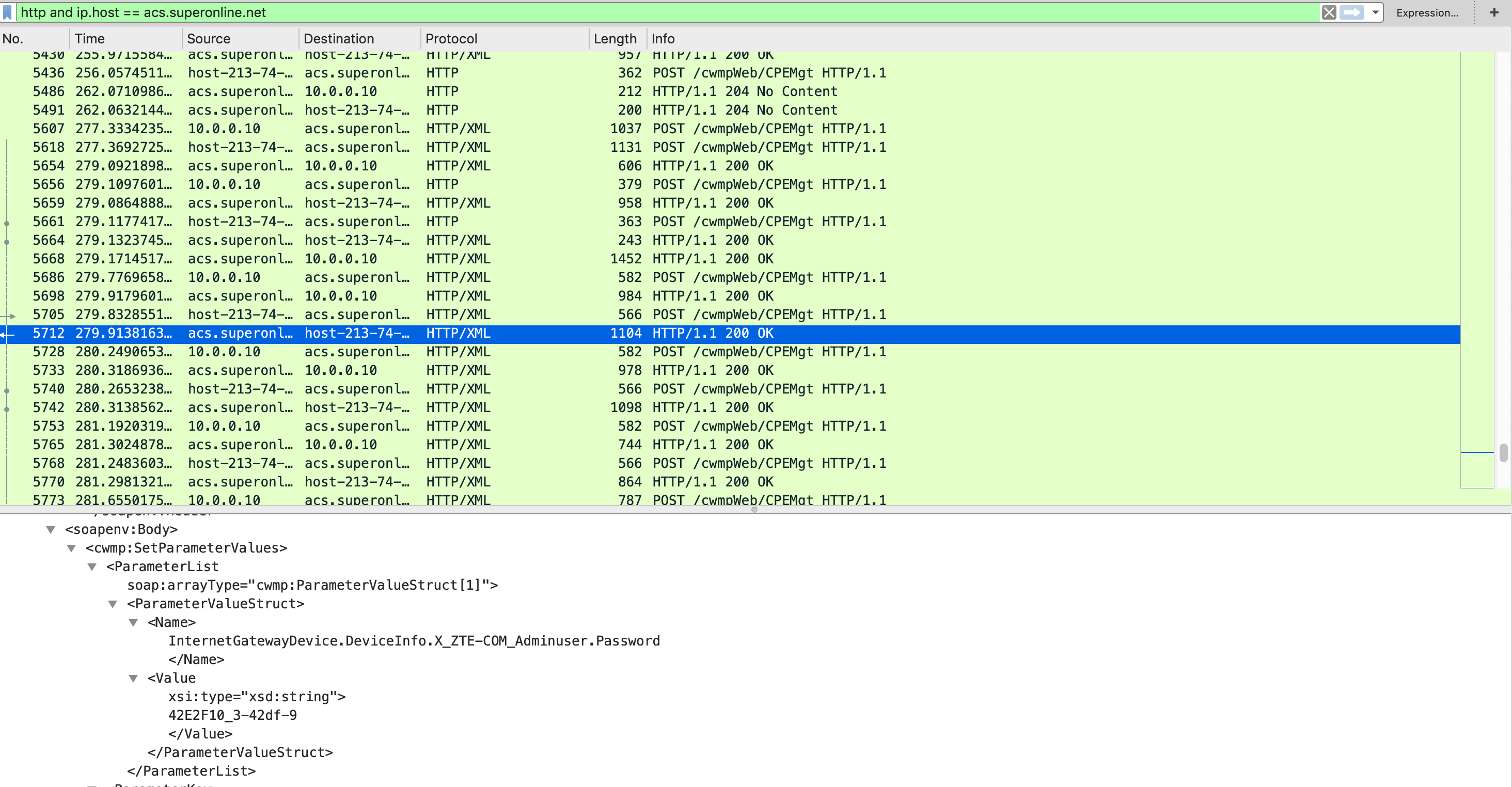
As you can see from the results, the configuration server returned the password. The thing is, this password is not static, it changes every time you reset your router so you have to find it again and again if you don’t stop TR069 connection.
Finally, I gathered the password but whenever I reset the router, the password will be changed as well. To prevent that I needed to find the firmware and its original root password.
Searching for the Firmware
We need the configuration server to tell the firmware location. And to do that we need configuration server to think our router has a different version than its latest version.
I checked the requests and found out that, the router sends information about its hardware, software, name e.g.
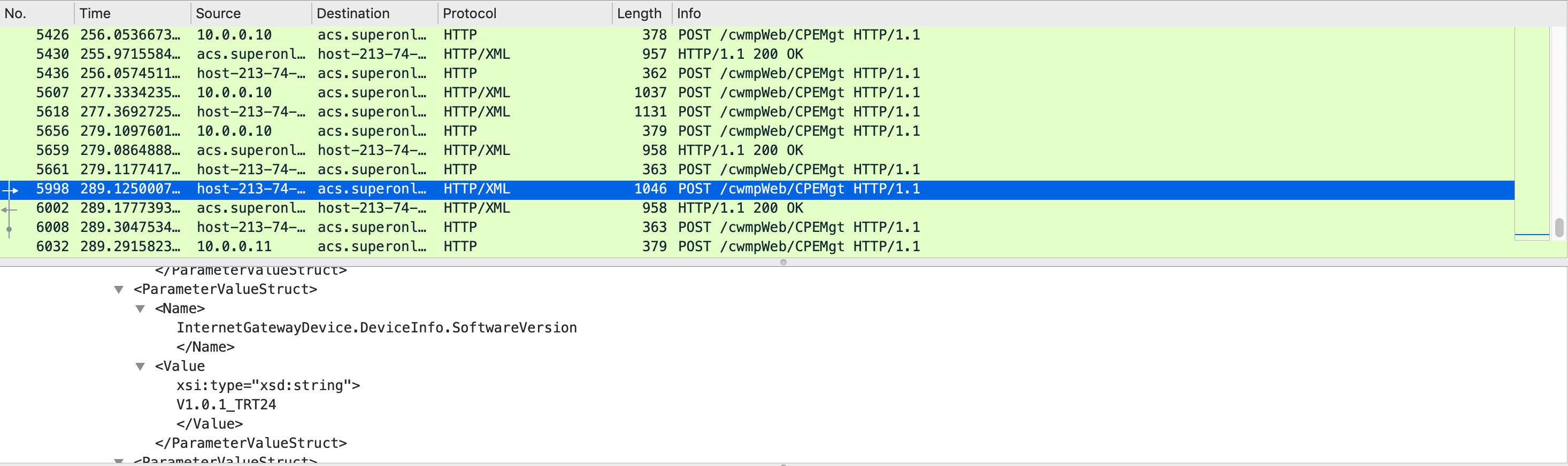
So if I could replace this value in the request, I could get the firmware. First of all, I stopped the mitmproxy and started it with another set of parameters. The meaning of the newly added parameter is to filter only request bodies, if there is a matching string with the first part, replace it with the second part.
|
|
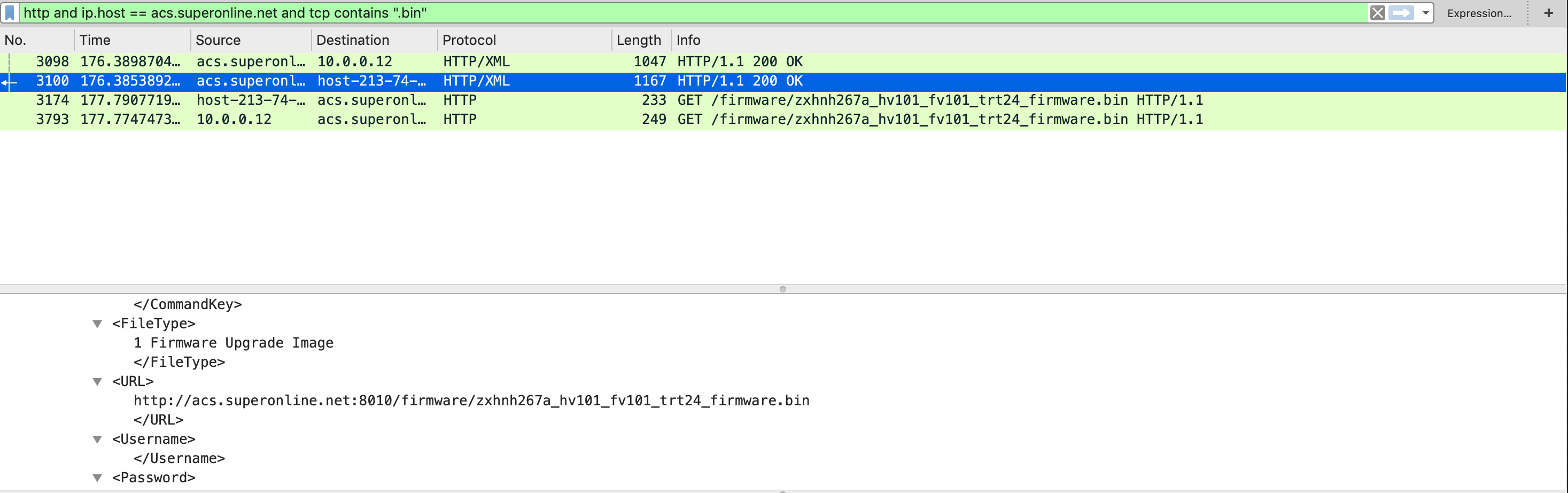
As you can see from the results, the configuration server sent the firmware location.
Conclusion
In these blog posts, I explained all the steps to find your root password and the original firmware of the device.
I also tried to capturing the original root password. To do that, I altered one of the responses and forced the router to send its password. Unfortunately, there is no password assigned to root user, and as far as I can tell without a password, UI does not let you log in.
Completing all of these steps is not easy for everybody, and it takes lots of time.
And also, there is no way to log in as root without doing all these steps above.
To reduce the complexity and required time, I am planning to develop an application that shows all the information, and sets the root password without too much hassle.